Business Email Compromise: The Silent Cybercrime Costing Millions in 2025
- David Chernitzky
- Aug 6, 2025
- 4 min read
Updated: Dec 22, 2025

In 2025, one of the most financially devastating cyber threats isn’t ransomware — it’s Business Email Compromise (BEC).
While ransomware may still dominate headlines, BEC is quietly draining billions from businesses worldwide through sophisticated social engineering and email-based deception. Unlike attacks that rely on malware or encryption, BEC preys on human trust — impersonating executives, hijacking vendor threads, and slipping into financial workflows undetected.
Cybercriminals are going straight for the inbox, bypassing technical defenses and exploiting gaps in awareness and process.
So what exactly is BEC — and why has it become one of the most dangerous and costly cyber threats today?
What Is Business Email Compromise (BEC)?
Business Email Compromise is a type of cyberattack where threat actors impersonate a trusted person or entity via email to manipulate victims into transferring money or sensitive data.
BEC isn’t just spam — it’s highly targeted social engineering. And it works because it looks like business as usual.
Types of BEC attacks include:
CEO fraud: Impersonating an executive requesting urgent wire transfers.
Vendor email compromise: Hijacking a vendor's inbox to send altered invoices.
Payroll redirection scams: Posing as employees requesting changes to bank deposit info.
Attorney impersonation: Sending fake legal or settlement demands.
Why BEC Is One of the Top Threats in 2025
It’s low-tech, high-reward.
BEC attacks require no malware, so they often bypass traditional antivirus and firewall systems.
It’s skyrocketing in cost.
According to the 2024 FBI IC3 Report, BEC losses exceeded $2.9 billion, surpassing ransomware, phishing, and crypto scams combined. Early 2025 figures suggest this trend is accelerating.
It’s evolving fast.
Modern BEC uses AI to clone writing styles, spoof email threads, and even generate fake voice messages.
It’s targeting your finance team and executives.
Unlike bulk phishing, BEC goes after the people who move money — CFOs, accounting, HR, and executive assistants.
How a BEC Attack Unfolds
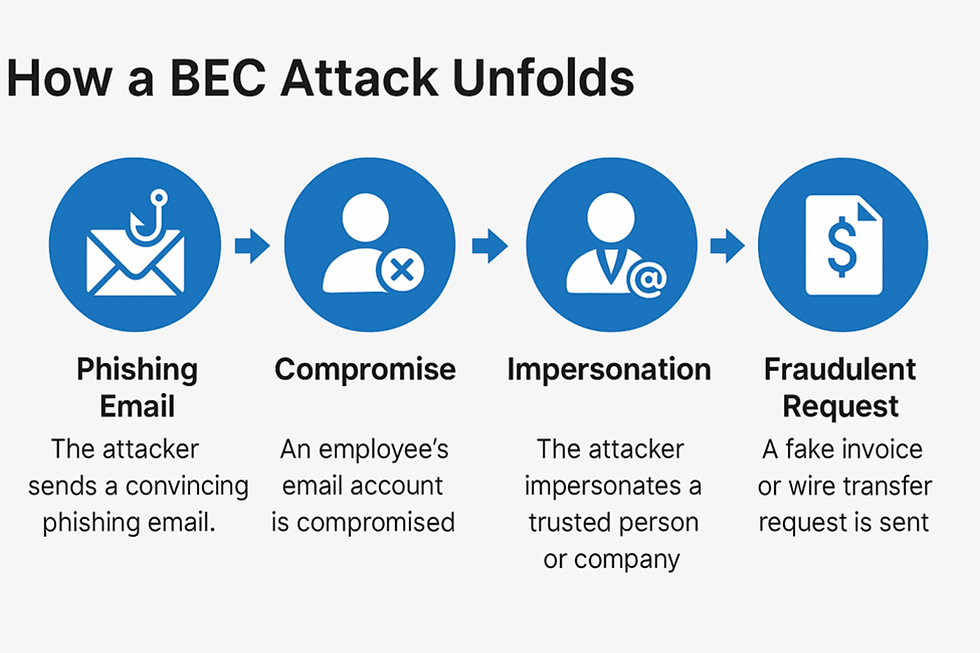
Reconnaissance: Attackers study your company’s structure, vendor relationships, and email habits via social media, past breaches, and open-source intelligence.
Spoofing or Compromise: They create lookalike domains or hijack a real email account via credential theft or session hijacking.
Execution: A perfectly timed, urgent-sounding email is sent to a target — often right before a weekend, holiday, or executive travel.
Exfiltration: Funds are wired to a fraudulent account, usually overseas. By the time it's discovered, it’s too late.
Warning Signs of a BEC Attack

The Real Cost of BEC
The average cost of a BEC attack in 2025 is $50,000, contributing to an estimated $6.3 billion in global losses, according to the 2024 Verizon DBIR. Unlike ransomware — where data can often be restored from backups — BEC attacks involve real-time financial fraud. Once funds are transferred, recovery is complex and time-sensitive.
While some organizations have been able to recover stolen funds through rapid banking intervention or with the help of cyber insurance, success is never guaranteed — and in many cases, the money is permanently lost.
How to Protect Your Business from BEC in 2025

Why Cyber Insurance May Not Cover BEC Losses
Many businesses assume cyber insurance will cover all types of digital threats. But when it comes to Business Email Compromise, the reality is more complicated.
In recent years, cyber insurance claims related to BEC have faced increased scrutiny and, in some cases, denial, particularly when policies exclude social engineering or require strict internal controls. BEC remains one of the more complex scenarios for insurers to evaluate.
The fraud is classified as a voluntary transfer of funds rather than a technical breach
The company fails to follow the required verification procedures
There’s a lack of documentation showing that protocols (like dual approval or callback verification) were followed
Several high-profile lawsuits have emerged in the past year where insurers refused to pay out on BEC claims, citing exclusions or procedural gaps.
What Can You Do?
1. Review your cyber policy — Understand what is and isn't covered regarding BEC and social engineering fraud.
2. Check for social engineering endorsements — Many policies require add-ons to cover BEC and invoice fraud specifically.
3. Document your controls — Insurers often require proof that best practices (dual authorization, training, verification steps) were followed.
4. Train your finance and HR teams — These are the most common points of failure — and scrutiny — in BEC-related claims.
BEC and the Role of Awareness Culture
Technology alone won’t stop BEC. Attackers exploit human behaviour, not just systems.
That’s why cyber awareness training — especially for finance, HR, and executives — is more critical than ever. When employees pause, report, and verify instead of reacting, the BEC chain is broken.
BEC success depends on silence. Reporting suspicious emails loudly and early gives your team the power to stop it in its tracks.
Final Thoughts
Business Email Compromise may not make flashy headlines, but it’s draining businesses of billions, one email at a time. It’s silent, it’s personal, and it’s on the rise.
The good news? With the right mix of awareness, controls, and communication, BEC can be stopped before the damage is done.
Don’t wait for the fake invoice to hit your inbox.
Build a response. Build awareness. Build resilience.
Frequently Asked Questions (FAQs)
Q: How long can attackers monitor email conversations before launching a BEC attack?
A: Some attackers observe internal and vendor email threads for weeks or months to learn tone, timing, approval patterns, and payment cycles before sending a fraudulent request.
Q: Can BEC attacks occur without any email accounts being compromised?
A: Yes. Many BEC attacks rely entirely on impersonation and lookalike domains, meaning no systems are breached and no malware is involved.
Q: Are certain times of year more vulnerable to BEC attacks?
A: Yes. Quarter-end closings, holidays, executive travel periods, and peak payroll cycles are especially attractive to attackers due to urgency and reduced verification.



Comments