Tabletop Your Worst Day: Breach Simulations That Actually Improve Readiness
- David Chernitzky
- Dec 15, 2025
- 6 min read
Updated: Dec 22, 2025

When a cyber breach strikes, time seems to distort. Minutes feel like seconds. Information is incomplete or conflicting. Your team looks to leadership for direction, while customers, partners, regulators, and even the media begin demanding answers. For many small and mid-sized businesses, this moment—the first chaotic burst of a cyber incident—determines whether the company recovers gracefully… or spends months in turmoil.
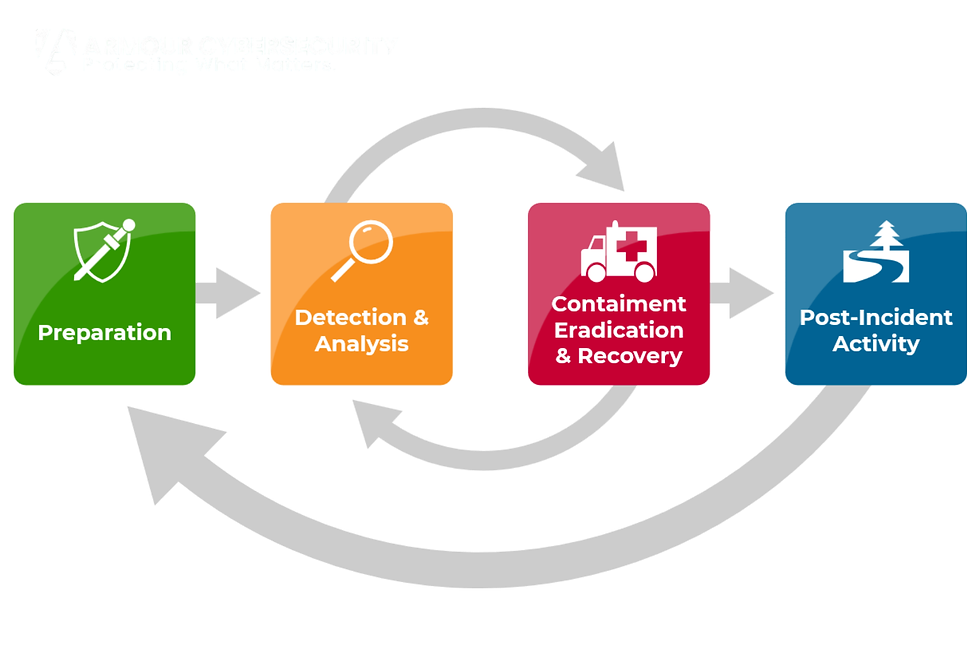
This is the reality that incident response tabletop exercises and breach simulations are designed to prepare you for. They offer a controlled environment to experience your organization’s “worst day,” but without actual systems shutting down or data being encrypted. Yet, just like a fire drill, the value depends entirely on how realistic and immersive the exercise is. Many companies run tabletops that amount to little more than a meeting with a scripted scenario. These have little power to improve resilience. What organizations truly need—especially today—are simulations that expose gaps, refine processes, test decision-making, and strengthen alignment across every level of the business.
Why Breach Simulations Matter More Than Ever
Cyberattacks have evolved into sophisticated, business-disrupting events. Modern ransomware groups operate like professional enterprises with dedicated negotiation teams, multilingual support, and deep networks of affiliates. For SMBs, which often rely on lean IT teams, this landscape poses a serious challenge. Incident response plans may look solid on paper, but if they haven’t been tested, they’re likely full of assumptions that unravel under real pressure.
A breach simulation brings those assumptions into the light. It reveals whether your incident response (IR) plan, roles and responsibilities, and communications processes are ready for the real world. Perhaps your team isn’t sure who contacts the insurer. Maybe backups exist—but aren’t accessible. Maybe executives disagree on whether to shut down systems. Or maybe legal obligations differ across regions, especially when dealing with Canadian privacy laws or LATAM compliance frameworks. A good simulation uncovers these gaps early, giving your team time to strengthen its posture long before a real attacker puts it to the test.
What an Effective Tabletop Really Looks Like
A high-quality breach simulation is dynamic, unpredictable, and deeply rooted in real attacker behavior. It challenges the technical team’s ability to assess and contain the threat, but it equally challenges leadership to make timely and difficult decisions. While IT works to understand what systems are affected, executives must weigh business continuity, regulatory exposure, financial risk, and public perception. The communications team must craft responses under pressure, often without complete information. Legal counsel must guide decision-making to preserve privilege and maintain compliance with reporting timelines.
This interplay—the merging of technical, legal, operational, and reputational concerns—is the core of an effective tabletop. It pushes participants out of their comfort zones and forces them to collaborate under realistic constraints. When done correctly, it exposes not just procedural gaps but also deeper issues such as unclear lines of authority, slow escalations, or mismatched expectations among stakeholders.

The Scenarios That Build True Readiness
Different organizations benefit from different types of simulations, but a ransomware-focused exercise remains the most impactful for most SMBs. It mirrors what many businesses face today: encrypted servers, halted operations, and a ransom note that puts leadership under immediate pressure. A scenario like this forces teams to decide whether backups are usable, whether the ransom will be considered, how customers will be informed, and how quickly recovery can begin.
Executive tabletops, by contrast, step away from the technical details and focus on high-level decision-making. Leaders must think strategically—balancing legal obligations, reputation management, financial impact, and long-term recovery. These exercises help uncover whether leadership understands the IR plan and its own role within it.
For organizations in Canada and LATAM, regionalized scenarios are vital. Laws governing breach reporting vary widely. A simulation tailored to those environments helps ensure that legal obligations, cultural expectations, and multilingual communications are handled appropriately from the first moment of the crisis.

How a Well-Designed Simulation Drives Real Improvement
A powerful breach simulation doesn’t begin and end with a story on a slide. It starts with a carefully crafted scenario that unfolds gradually, introducing uncertainty and escalating consequences. Information is released in waves, just as it would be during a real attack. Participants must make decisions without perfect clarity, and each choice affects what happens next.
This process tests visibility gaps, backup strategies, and forensics readiness on the technical side. It also evaluates crisis communications workflows, insurer engagement, negotiation strategy, and cross-team collaboration. Throughout the exercise, facilitators guide the experience—not by providing answers, but by prompting participants to think critically, challenge assumptions, and adapt quickly.
But perhaps the most important outcome happens after the simulation ends. The after-action report (AAR) becomes the blueprint for improvement. It documents what happened, where delays occurred, what decisions were made, and what obstacles prevented an effective response. The AAR should provide a prioritized roadmap for strengthening policies, technologies, responsibilities, and coordination. It is the artifact that transforms a few hours of discussion into lasting operational resilience.
Why Many SMBs Struggle to Run These Exercises Alone
Smaller organizations often try to conduct tabletop exercises internally, but they quickly discover the limitations. Scenarios may be too simple, lacking realism or adversarial nuance. Participants may avoid challenging leadership decisions, reducing the authenticity of the discussion. Internal facilitators may not have the experience needed to push teams or connect decisions to real-world consequences. And without a structured process or a robust AAR, the lessons learned often fade away within days.
External specialists bring not just neutrality, but also deep experience drawn from real incidents. They understand how attackers think, how crises unfold, and where most organizations stumble. They also bring the structure needed to deliver measurable outcomes rather than just theoretical discussions.
How Armour Cybersecurity Delivers Truly Transformative Exercises
Armour Cybersecurity has built a breach simulation program specifically designed for SMBs across Canada, the United States, and LATAM. Our approach blends realistic threat intelligence with deep experience in incident response, legal guidance, and crisis communication.
We begin by learning about your business—your systems, your industry, your regulatory landscape, and your maturity level. From there, we craft tailored scenarios that reflect both emerging threats and regional nuances. Our facilitators, who include former incident responders, forensic analysts, communications experts, and Canadian and LATAM breach coaches, guide your team through a structured, immersive exercise that challenges each participant in their role.
During the exercise, we ensure engagement across all levels—from the technical responders to the executive leadership team. We highlight decision points, illuminate risks, and test assumptions without disrupting your day-to-day operations. After the simulation, we deliver a detailed, professional after-action report, complete with timelines, lessons learned, remediation recommendations, and actionable improvements for your cyber crisis playbook.
The result is not just a better incident response plan, but a more aligned, coordinated, and confident organization—one ready to face a breach with clarity and resilience.
Are You Ready to Prepare for Your Worst Day—Before It Happens?
A breach is no longer a distant possibility. It is a predictable part of operating in today’s digital landscape. But preparedness is not about fear—it’s about confidence. When your team has rehearsed the roles, decisions, and communications required during a crisis, your organization moves faster, communicates more clearly, and recovers more effectively.
Armour Cybersecurity is here to help you build that readiness through high-impact breach simulations and tabletop exercises that reflect real threats and real consequences.
Contact Armour Cybersecurity today to schedule a tailored breach simulation and strengthen your incident response capabilities. Your worst day may be inevitable—but with the right preparation, it won’t define your organization’s future.
Frequently Asked Questions (FAQs)
Q: Who should participate in a breach simulation beyond IT and security teams?
A: Effective simulations often include executive leadership, legal, HR, communications, finance, and third-party stakeholders to reflect real-world decision-making.
Q: How often should organizations run breach simulation tabletop exercises?
A: Most organizations benefit from running tabletop exercises at least once a year, but higher-risk environments (regulated industries, frequent system changes, or active threat landscapes) often run them quarterly or biannually. The right cadence depends on how quickly your technology, team structure, and threat profile change.
Q: Are tabletop exercises useful for smaller organizations?
A: Absolutely. Smaller organizations often have less redundancy and fewer resources, making clear roles and fast decisions even more critical. Tabletops can be scaled to size and help smaller teams uncover single points of failure before a real incident occurs.



Comments